Shift Left Security Testing – Learn Its Importance & Best Practices
Artificial Intelligence and Machine Learning are driving today’s tech world. They are increasingly becoming important for every industry, especially the application development industry. However, when the development of Apps is on its way to changing the lives of people it used to be, hackers have found their soft spot & turned their attention to exploiting vulnerable apps. Thus, tight security integration throughout the Software Development Life Cycle (SDLC) is required. That’s when Shift Left Security Testing comes into the picture. Guaranteeing application security at the earliest stages in the SDLC.
Let’s dive in and explore more about this security testing approach.
What is Shift Left Security Testing?
Shift-Left Security Testing is the practice of integrating DevSecOps shifts into the SDLC as early and frequently as possible. Early-stage vulnerabilities are generally simpler and less expensive to resolve.
Organizations are looking for ways to integrate security into the development process so that developers can produce trustworthy solutions without having to become security specialists themselves and without delaying the process of creating new applications. By dramatically lowering the security concerns associated with the creation of cloud-native software and applications, Shift Left security assists them in achieving this.
Understand The Importance of Shift Left Testing
By moving security to the left, security teams may serve as a supporting role, providing developers with the knowledge and tools they need to work independently while also providing the organization with the necessary level of monitoring.
With the rapid advancement of modern technology, both the speed of product delivery and the value of making decisions on one’s own without the assistance of a third party have increased significantly.
Security teams now confront more demands as a result of the expansion of the organization as a whole, which frequently slows down the rapid development cycle.
This was caused by elements like outdated application security tools and procedures that were created for the sluggish, pre-cloud age. And as a result, it is now the developers’ obligation to choose and put in place the proper security barriers for their process.
Challenges Faced While Trying to Shift Security Left
Teams attempting to move security to the left frequently run into the following problems:
- A lack of knowledge of common security flaws. Knowing the most common cyber security threats and being able to stop them is essential for effective code hygiene.
- Collaboration with the infosec team is lacking. The InfoSec team is crucial to the implementation of security, thus leaving them out of the development process is a big problem in today’s world when threats are developing at the same rate as technology.
- The Infosec team’s delayed involvement. The Infosec team typically doesn’t get involved until after the SDLC. In terms of making adjustments to the “vulnerable” product that has already been published, such situations are quite expensive.
- Lack of information security personnel required. Information security teams are reportedly frequently understaffed. Even big businesses only have 1 infosec employee for every 10 persons who work in infrastructure for every 100 developers.
Though there are a few issues faced while implementing shift left security, the good thing is there are various benefits associated with it. Let’s have a look at those.
Benefits of Shift Left Security Testing
Testing to the left has a variety of advantages, including the following:
- Faster delivery. When testing is incorporated into the pipeline, software delivery speed is increased. Before deployment, bugs are found and resolved, freeing developers to concentrate on releasing new features.
- A stronger focus on security is placed from the design phase forward. From creating, deploying, and safeguarding production workloads, security is closely integrated thanks to a shared responsibility approach.
- Cost savings. Finding defects and vulnerabilities prior to deployment dramatically lowers risk and operational expenses.
- Enhancing security integration and speed. By doing away with the need to retrofit security controls after creation, secure software delivery costs and lead times are decreased.
- Enabling higher overall business success. Adopting new technologies and having more confidence in the security of produced software allows for increased revenue growth and extended service options.
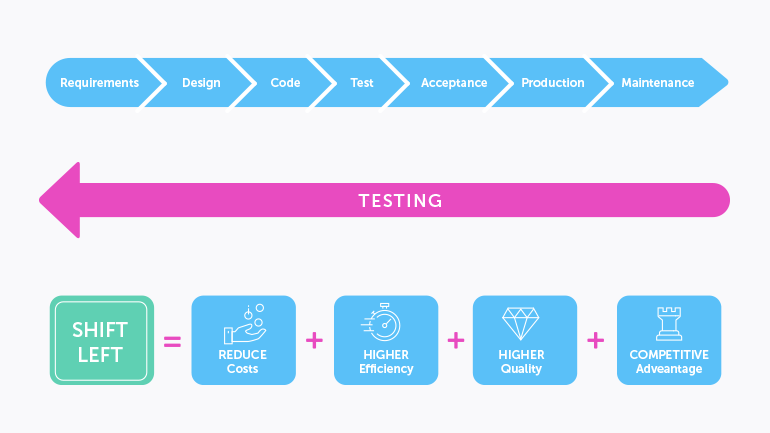
[Image Source: Testim]
Common Shift Left Security Testing Tools
To avoid adding more security threats than the operations and security teams can handle, DevOps organizations realized they needed to shift security left as well. DevSecOps is a movement that bridges the security assessment gap and enables quick, automated security evaluation as part of the Continuous integration and continuous deployment (CI/CD) pipeline.
Some of the most popular shift left security tools are discussed below:
- Source code is examined using Static Application Security Testing (SAST) to look for known flaws and unsafe development techniques. DevSecOps typically incorporate this testing to give developers’ development environments real-time feedback on security threats.
- Software Composition Analysis (SCA) examines software to locate the open source and third-party libraries as well as other well-known software components, as well as any associated vulnerabilities. By identifying vulnerabilities that cannot be found by scanning source code, SCA enhances SAST.
- Prior to deployment into production environments, programs are scanned during dynamic application security testing (DAST). This makes it possible to examine apps from the outside for exploitable circumstances that could not be found in a static state.
- In the production environment, RASP (Runtime Application Self-Protection) runs side-by-side with applications to monitor and analyze behavior and warn of or stop unauthorized and anomalous actions. This offers real-time visibility into potential application security concerns, however, it might place extra load on the infrastructure of the production settings.
- The use of Web Application Firewalls (WAF) allows for the monitoring of application-level traffic in order to identify potential attacks and efforts to exploit security holes. Even without fixing the underlying software flaws, WAFs can be set up to prevent specific possible attack paths.
- Container image scanning systems can automatically and continuously scan container images in container registries and across the CI/CD pipeline prior to deployment into production environments. This enables the discovery of defects or potentially harmful components and provides developers and DevOps teams with explicit guidance on how to correct them or lessen their consequences.
Solutions for Cloud Security Posture Management (CSPM) find configuration errors in cloud infrastructure that can leave possible risks and attack vectors unchecked. Based on internal policies or external security standards of an organization, CSPM solutions can suggest or automatically implement security best practices.
Shift Left Security Best Practices to Follow
The following procedures can be followed for shift left security testing.
- Define shift left security policies: Security policies are an excellent place to start when it comes to shifting left security. Policies can give vital information for effective development processes, including security, by automatically and consistently establishing boundaries before work begins.
- Examine where and how software is produced: It seems sensible to reevaluate your SDLC as your engineers get more familiar with secure coding techniques. It will be easier to identify simple measures you can take to incorporate testing earlier in the lifecycle once you have a better understanding of where and how your software is generated. You can also discover what tools might be useful for your codebase.
- Adopt security automation: Development teams ought to adopt security automation software. Application and system external risks can be automatically detected, looked into, and fixed using security automation’s software-based methods. Automation shortens the time to market by accelerating the development lifecycle.
- Apply security updates as code is written: In a perfect world, you would integrate security into the development process as it happens and respond to input right away. Developers can swiftly apply fixes by receiving feedback on the code they are working on in this way.
- Integrate visibility into the culture: Shift left security places a strong emphasis on maintaining the security of the code both during and after release. Teams must maintain ongoing insight into application security to accomplish this. Then, they can provide software upgrades to address problems as they arise.
Conclusion
Conducting vulnerability assessment and penetration testing post-product launch could cost more time and money for the organization. Hence, the shift left security testing approach is required to fill the security gap (if any) at the earliest stage of application development.
For any kind of cybersecurity-related assistance, contact our team now.
FAQs
Q. In shift-left security testing, what function does threat modeling serve?
One essential part of shift-left security testing is threat modeling. Early on in the design process, it entails detecting potential security risks and weaknesses. Development teams can handle security issues proactively and produce software that is more resilient by implementing threat modeling.
Q. What is the effect of containerization on shift-left security testing?
Certain security considerations are introduced by containerization. Shift-left security testing needs to encompass evaluations of container security, encompassing vulnerability scanning of images, runtime security, and guaranteeing safe configuration procedures for container orchestration systems.
Q. What role does API security play in the shift-left theory?
Shift-left testing requires API security, particularly in contemporary apps that heavily depend on APIs. To make sure APIs don’t bring vulnerabilities into the system as a whole, security testing should include checks for correct authorization, data integrity, authentication, and encryption within APIs.
Q. What precautions must be taken during shift-left testing to safeguard sensitive data?
A: Using strategies like data masking, encryption, and making sure secure coding practices are followed are important steps in safeguarding sensitive data during shift-left testing. To avoid unwanted access to sensitive data, access restrictions, and permissions should also be thoroughly tested.

